Sacrifice time spent on day-to-day tactical concerns to build a comprehensive strategic plan that aligns cybersecurity with business objectives.
- Gartner client? Log in for personalized search results.
It’s high time to acknowledge the link between cyber risk and business risk
Non-executive directors increasingly consider cyber risk a threat to shareholder value. However, many cybersecurity functions fail to adapt their strategies when business objectives change. The strategic planning process remedies this, clearly linking business drivers, objectives, gaps, projects and actions.
Strategy planning is the secret to an effective cybersecurity program
Strategy planning for the cybersecurity function must include best practices that are unique to the security discipline.
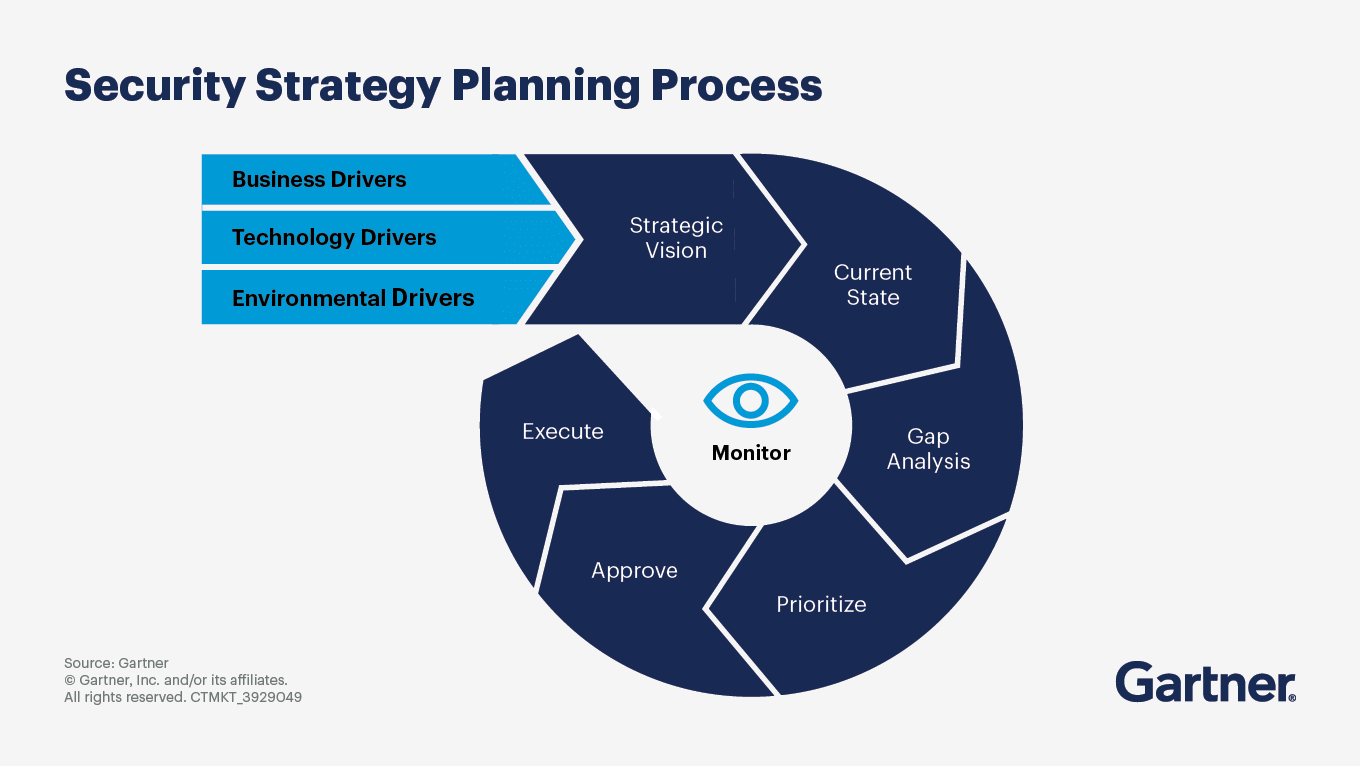
Steps No. 1 and No. 2: Capture the business context and define the strategic vision
Start by documenting the drivers that represent the overall business strategy:
Business drivers include competitive differentiators, market-share growth strategy, mergers and acquisitions strategy targets and product strategy.
Technology drivers include cloud adoption strategy, AI adoption strategy, data center consolidation and technology platform consolidation.
Environmental drivers include economic downturns and recessions, sociopolitical unrest, trade wars and impending regulatory changes.
Next, define the strategic vision ─ what the cybersecurity strategy seeks to accomplish over a specific time period. Develop a series of objectives that support progress toward the end goal. The primary objective should be an iterative process for planning, developing and managing security solutions that align with business requirements. Other objectives may be:
An overall maturity level for the program
Target maturity levels for specific controls, processes and functions
An accepted level of risk exposure within a risk appetite range set by executive leadership
New capabilities and architectures for changing technology realities
Ability to support the enterprise growth strategy
Steps No. 3 and No. 4: Assess the state of security and risk, and perform a gap analysis
Assess the effectiveness and efficiency of the cybersecurity program, then summarize your findings in a “current state” section of the strategic planning document. Assessments may include:
Vulnerability assessments and penetration tests to evaluate technical infrastructure
Risk assessments that balance the investment in controls that are appropriate to actual risks
Recent audit findings
Control effectiveness assessments to determine the maturity of control implementation; benchmarked to peers and aligned with industry standards
Capability maturity assessments to evaluate and benchmark the maturity of cybersecurity processes and programs
Cybersecurity spending and staffing benchmarks to compare resourcing with peers
A gap analysis involves mapping the current state against the vision statement, objectives, and key business, technological and environmental drivers. Once you’ve found the gaps between the current and desired states, you can formulate plans to bridge those gaps.
Steps No. 5 and No. 6: Prioritize proposed actions, and get executive approval and budget
There are only so many hours in a day and resources to spare, so prioritize the list of necessary actions revealed by the gap analysis. Consider these criteria:
Level of risk reduction a given project or activity may achieve
Resources required to execute identified projects
Expected financial cost
Time to value
Choose a mix of projects ─ some promising a short time to value and some requiring longer timelines. Break long-term projects and initiatives into smaller projects with phases and milestones.
Finally, present a report and a presentation to executives to get approval and most important, budget. Demonstrate how the strategy will contribute to business value by linking proposed projects to the business strategy. Go into detail about the phases and milestones that will move the cybersecurity function to the desired state. Consider using benchmarking data to substantiate the business case.
Post-planning: Execute the plan and monitor results
Continuous, transparent reporting is key to maintaining executive support for the security program. There’s more than one way to report progress: Consider using a balanced scorecard, governance, risk and compliance (GRC) reports or in-house dashboards that use outcome-driven metrics. Credible reporting includes:
Expected benefits that were fully or partially realized
Expected benefits that were not realized
Unexpected benefits
Unexpected issues or disadvantages
Projects for which the jury is still out
Triggers to security responses or challenges that may require changes to the strategy
Reporting can surface problems that require a change in strategy, so schedule progress reports on a quarterly basis to stay agile. Pair these reports with scenario-planning workshops that capture internal and external changes. Use the output of these workshops to inform the C-suite of trends that require major security strategy and roadmap changes.
Cybersecurity strategy FAQs
What is cybersecurity strategy planning?
Strategic planning is fundamental to developing, managing and advancing a cybersecurity program. A cybersecurity strategy establishes the medium- to long-term direction of the cybersecurity program. It details how an organization’s capabilities will support and enhance its corporate strategy and digital trajectory and respond to relevant changes to the external environment such as social, economic, business, regulatory, political and technological shifts.
What makes a comprehensive cybersecurity strategy?
To be successful, cybersecurity leaders must consider relevant factors such as business, technology and environmental drivers along with business context, resource requirements, potential constraints and execution risks when designing a cybersecurity strategy.
Drive stronger performance on your mission-critical priorities.