Use zero-trust architecture and an identity-based cybersecurity approach to evolve your perimeter-based defenses.
- Gartner client? Log in for personalized search results.
Implement Zero-Trust Architecture to Adapt to a Shifting Threat Landscape
Develop a zero-trust communication story that works
Often, cybersecurity fails to deliver on zero-trust initiatives due to miscommunications with the team supporting this approach to defending the business. Typically it’s due to ineffectively communicating the benefits of zero-trust architecture to key stakeholders.
Download this conversation guide to:
Communicate zero trust’s benefits to nontechnical leaders, such as other C-suite executives
Communicate and gain buy-in from technical leaders
Engage architects in discussions about zero trust
Mature your cybersecurity program with zero trust capabilities
Enhance your organization’s ability to securely connect users to applications by tackling four key areas.
Why Zero Trust?
4 Areas of Zero Trust
Get Started With Zero Trust
Zero trust is a modern approach to mitigating risks and impacts of cyberthreats.
CISOs are exploring zero trust as a way to facilitate proper access to resources while limiting lateral movement of adversaries in an environment of increased cyberattacks and an ever-growing number of access points. In contrast to the traditional “castle and moat” model of information security, where everyone inside the moat is implicitly trusted, zero trust assigns access based on calculated risk and adapts the access as the calculated risk of the entity changes and the criticality of the accessed object.
The zero-trust approach delivers the resilience to mitigate cyber risk, enables modern business capabilities and a hybrid workforce, and provides the flexibility to enable appropriate access methods, while removing implicit access based on location. It is garnering sufficient interest that by 2026, 10% of large enterprises will have a mature and measurable zero trust program in place, up from less than 1% today.
Vendors are responding to the growing attention on zero trust by marketing the concept. But zero trust is not a product that organizations can buy. Instead, it is mindset or set of principles. Nor can zero trust solve every security challenge the organization has. Instead, it has the following technical strengths and weaknesses:
Zero trust strengths:
Replaces implicit trust with explicit trust based on identity and context
Securely connects entities to resources. This allows you to securely connect users to applications, and limits nonuser devices to authorized resources only
Enforces a consistent and dynamic approach to protect resources
Visualizes which users are accessing which applications, which helps adhere to the access principle of “just in time” and “just enough”
Drives consistent security posture and consistent access policies, regardless of user, device or location, while minimizing user friction by matching authentication with risk
Limits lateral movement of threat actors or malware within your organization by pushing access decisions close to the resource
Enhances system confidentiality by enforcing encryption for all data in motion
Zero trust weaknesses:
Employee resistance, as some will find the approach overly restrictive
Long deployment times
The potential for mistakes in contextual decisions that incorrectly drop user connections, causing random or inopportune loss of access
Does not: Prevent software supply chain attacks; protect public-facing applications; offer 100% assurance the right user is behind the account; generally protect access to SaaS applications; fix or compensate for poor access policy
Complexity can ramp up quickly if automation and good processes are not ingrained
Requires a well-developed exception process that can be executed quickly for critical access
The policy decision point (PDP) is a single point of control that could be compromised
Technical debt may prevent zero trust implementation everywhere
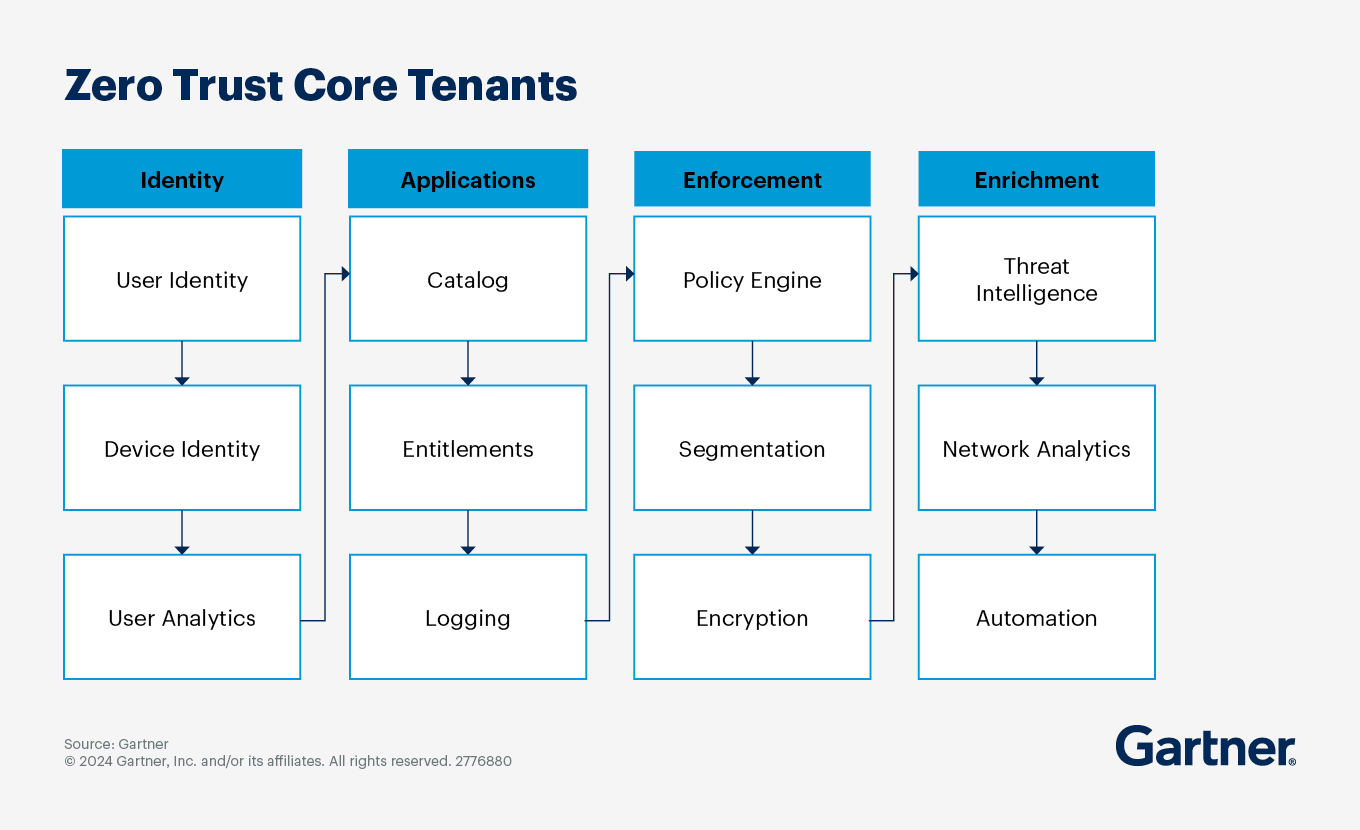
Focus on four areas for establishing and enforcing zero-trust architecture.
In its simplest term, zero trust is a way to securely connect users to applications through the devices they use to do their jobs. Organizations embracing zero trust should take action in the following four areas:
Identity of users and devices
Application governance and logging
Enforcement via technical controls and encryption
Enrichment with monitoring and automation
Area 1: Identity of users and devices
A critical function of a zero-trust model is to ensure that a user or entity has the proper level of authentication. Access to different resources may require different strengths of authentication, depending on how sensitive an application is.
As for devices, the more information you know about them, the better you can manage risk. For user devices, ask questions like, has it accessed applications previously? Does it meet basic hygiene requirements? For nonuser devices like Internet of Things devices, establish defaults such as denying devices access to the internet and documenting the resources these devices are permitted to access.
Area 2: Application governance and logging
To enable secure connections between users and applications, catalog the applications in the network, including the name and owner, level of data sensitivity and business criticality, business users and hosted location, among other details. Be prepared to spend considerable effort gathering information, including about nonsanctioned SaaS applications and about user-defined applications.
Once you know your applications, establish entitlements defining which users can access them at what level, and decide how these entitlements will stay up to date. Finally, establish rules around logging, including what to log, who can access logs, and how to back them up and ensure they cannot be modified.
Area 3: Enforcement
Once you know the identity of users and their entitlements, you must enforce the proper access. Common terms referring to devices that enforce access in a zero-trust environment are controller, broker, identity-aware proxy, microsegmentation and even firewall.
Microsegmentation is a particularly important concept in zero trust, as it is the ability to put a security service between any two workloads in your infrastructure, allowing you to isolate workloads and enforce access from end users to a workload or access from workload to workload
Perimeters also continue to play a role in zero-trust environments, though they should be more isolated so as to prevent lateral movement in your network to slow an attack and force the attacker to leave more traces. Encrypting all data in transit maintains confidentiality.
Area 4: Enrichment
Since user risk levels change over time, monitoring and logging are critical. Malicious insiders are one of our most dangerous threat actors, but whether attackers are internal or external, network detection and response (NDR) coupled with user and entity behavior analysis (UEBA) helps information security teams quickly find them.
Threat intelligence is another valuable enrichment that answers questions such as: What are the latest zero-day exploits? Or, what exploits are being heavily utilized? Design your zero-trust environment to ingest threat intelligence and determine which users and/or devices are affected.
Migrate to a zero-trust environment through iterative improvement.
Start your zero-trust journey by first tackling the following nontechnical tasks:
Define the strategy and zero-trust principles that your organization wants.
Identify the risks you are trying to address with zero trust, such as minimizing lateral movement or controlling the spread of ransomware.
Identify the scope of zero trust and the target for initial implementation, including any gaps and redundancies in technologies.
Secure the budget required.
Know your business processes. Be ready to add, change and possibly retire processes to maximize zero trust’s impact.
With those nontechnical aspects in place, take the following short-term actions, across the four areas.
User identity
In the short term:
Create a master directory with an identity governance and administration (IGA) function to ensure appropriate access.
Have a central identity provider (IdP) integrated with single sign on.
Ensure all access requires appropriate authentication.
Develop an automated process to review user entitlements.
Applications
In the short term:
Start building an application catalog.
Determine the business importance of the top 50 applications.
Enable logging to track critical application functions.
Enable encryption for critical applications at the application layer.
Device identity
In the short term:
Authenticate managed devices via a certificate from a trusted certificate authority.
Incorporate device hygiene into access decisions.
Ensure managed devices are acquired only via authorized channels.
Enforcement
In the short term:
Use security controls that can enforce access based on user identity.
Deploy products that can analyze network traffic to map users to applications
Attend a Conference
Experience IT Security and Risk Management conferences
With exclusive insights from Gartner experts on the latest trends, sessions curated for your role and unmatched peer networking, Gartner conferences help you accelerate your priorities.
Gartner Security & Risk Management Summit
National Harbor, MD

Frequently asked questions on zero trust
What is zero trust?
Zero trust is a security paradigm that replaces access based on implicit trust with access based on continuously updated identity and context. This facilitates securely connecting end users or other entities to resources. Technology vendors may use the term to associate their product with enhanced security capabilities.
Should I assume a breach?
Assume there will be constant attacks and that some will be successful. It is reasonable to assume that you will be breached. No network is 100% safe. Deploy controls to identify and then remove attackers when they get in. Segment your networks to limit damage until attackers can be removed.
Does zero trust reduce the organization’s network perimeter?
In some respects zero trust pushes the perimeter further out. Access to applications requires authentication, which has typically happened at the application server, with limited network controls to the server. Zero trust says we need to secure the network level. Users must identify themselves before they are allowed to connect to the application server. That extends the perimeter to the user.
Drive stronger performance on your mission-critical priorities.