Balance prevention with response and recovery to create a more sustainable and effective cybersecurity posture.
- Gartner client? Log in for personalized search results.
Cybersecurity Strategy: Embrace Fault Tolerance and Resilience
Plan a cybersecurity strategy that balances agility with business outcomes
The evolving threat landscape demands a dynamic approach to cybersecurity strategy. Yet, only 60% of teams adapt their strategies to shifting business priorities. The 2025 strategic roadmap for cybersecurity empowers CISOs and cybersecurity leaders to embrace innovation, adopt agile operations and manage risks effectively. Download now for:
Insights on cybersecurity’s current state
Key gaps and challenges
A comprehensive risk mitigation plan
Cybersecurity strategy best practices
Implement a cybersecurity strategy development process that maintains clear links between business and security objectives, and specific projects and actions.
Cybersecurity Strategy 101
Cybersecurity Vision
Cybersecurity Assessments
Cybersecurity Plan Buy-In
The cybersecurity strategy defines the vision and how to achieve it
Cybersecurity leaders are often so occupied by tactical challenges that they don’t take the time to engage in effective strategic planning. That is a mistake.
A concrete cybersecurity strategy sets out the medium- to long-term direction of the program. It outlines how the security organization will support and enable the corporate strategy and digital trajectory. It also helps the organization budget and document the rationale behind strategic decisions and resource allocation.
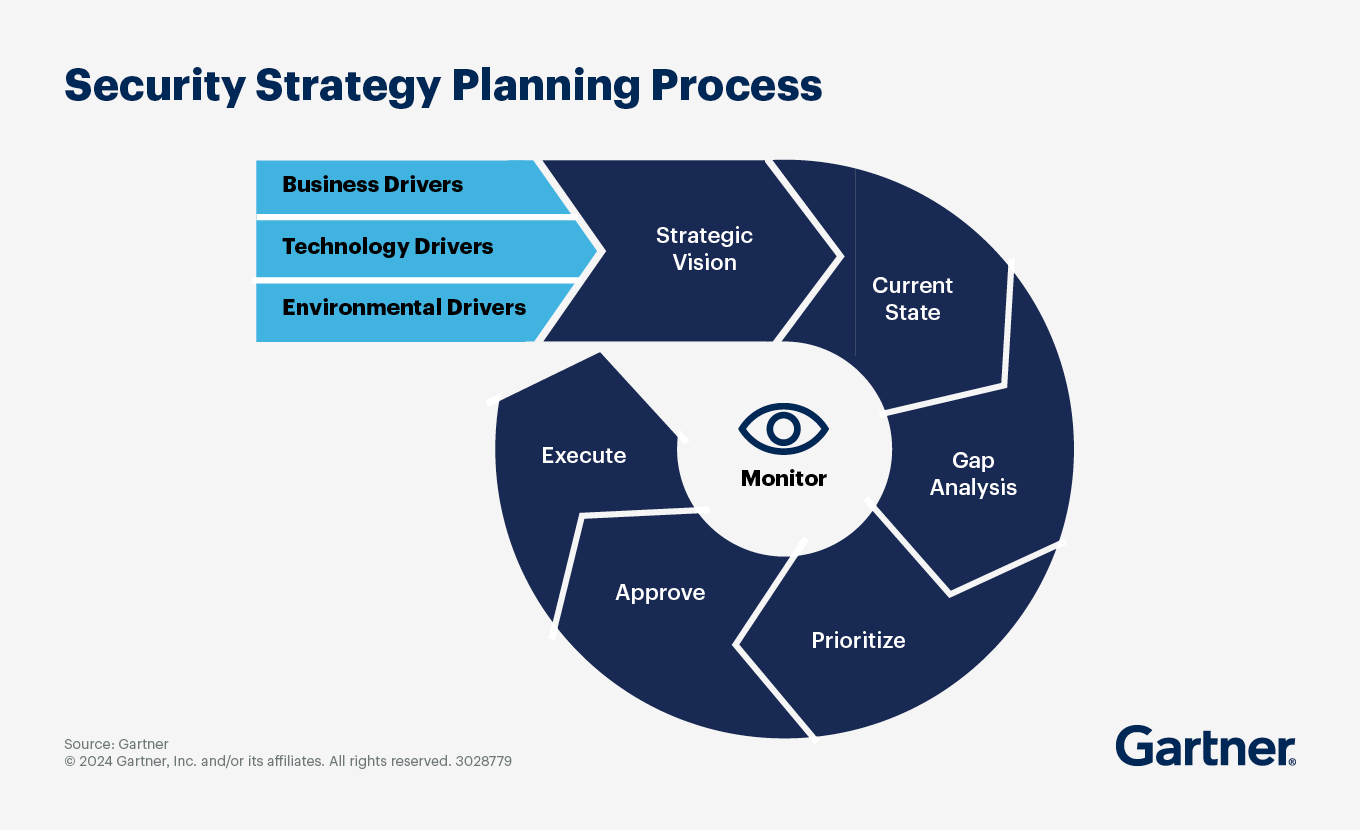
The building blocks of a cybersecurity strategy are similar to those of strategic planning processes. You must:
Articulate the strategic vision and business drivers.
Define the current state of cybersecurity in the organization, informed by maturity assessments, vulnerability assessments, risk assessments, audit findings and penetration tests.
Provide a prioritized roadmap that clearly links projects and corrective actions to the gaps, risks or vulnerabilities identified in the assessments, and to the relevant business, technology and environmental drivers.
With a documented vision, current state and roadmap, cybersecurity leaders can more clearly communicate with business leaders. An enterprise security steering committee should also review, discuss and approve security policy in a collaborative manner before formally documenting, disseminating and communicating it across the organization.
Define a vision based on business, technology and environmental drivers
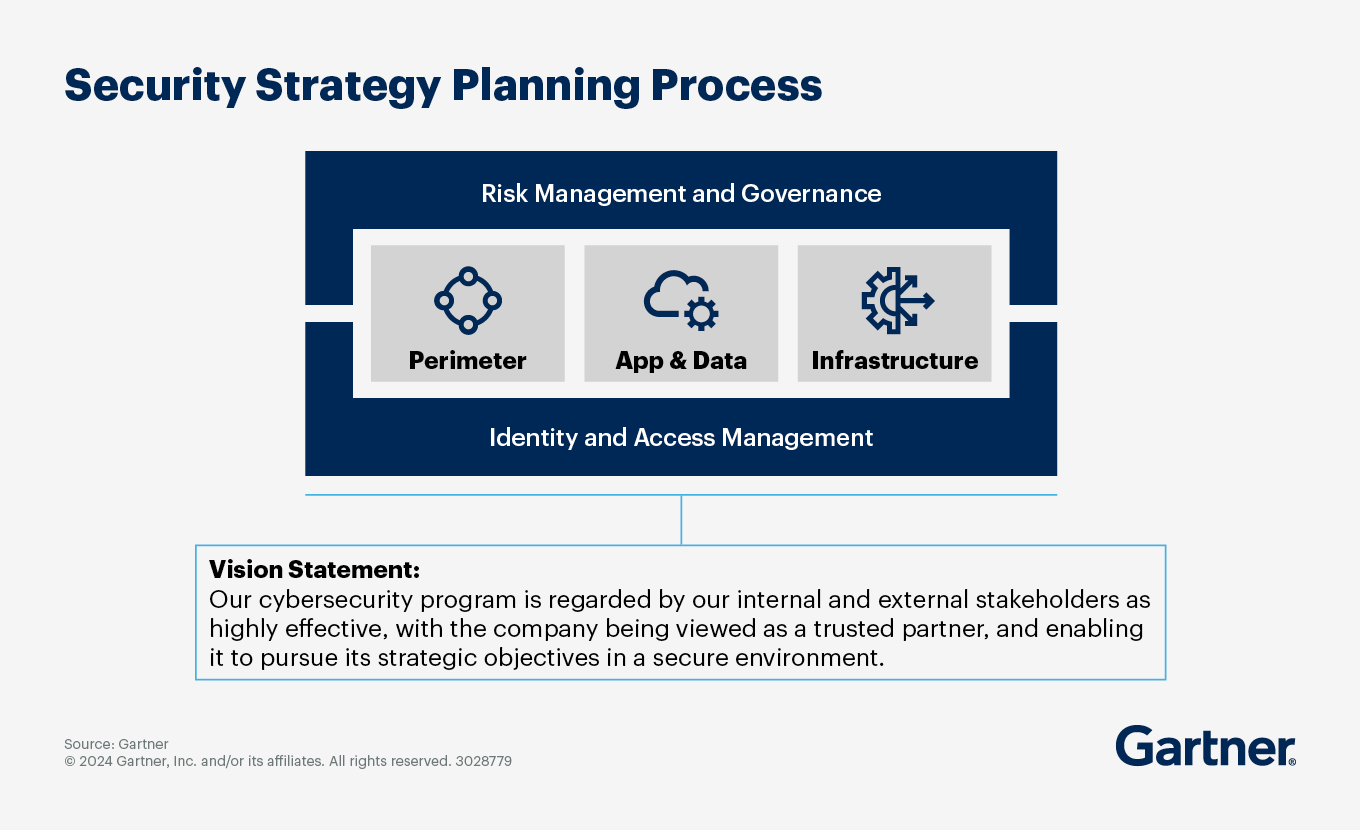
One of the most important elements of a cybersecurity strategy is the vision, which explains the objectives of the cybersecurity program in terms that business executives can understand and support. The strategic vision articulates the desired state that the cybersecurity strategy aims to achieve during the planning period.
Most organizations will base their vision on international standards, such as the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) or ISO 27001.
But don’t stop at standard elements. Incorporate relevant business, technology and environmental drivers specific to your organization. Example drivers include:
Business drivers:
Cost-cutting programs
Product diversification
Geographical expansion
M&As or divestitures
Technology drivers:
Digitalization strategy
Data center consolidation
Cloud adoption
Environmental drivers:
Economic downturns and recessions or growth conditions
Sociopolitical unrest
Geopolitical tensions, including trade wars
Impending regulatory changes
Include the specific cybersecurity objectives you want to achieve during the planning period as part of the vision. These objectives should include:
An overall maturity level for the program, and target maturity levels for specific processes and functions
A level of accepted risk exposure within an agreed risk appetite set by the executive leadership (include the defined risk appetite in the vision documentation)
New capabilities and architectures to address emerging threats or disruptive technologies
Support for the enterprise growth strategy — for example, a cybersecurity framework for integrating acquired organizations into the corporate security program
These objectives should be socialized and agreed on by key stakeholders, typically early in the cybersecurity-strategy planning process, as well as when leaders approve the proposed roadmap of priority initiatives. Work with the organization’s security steering committee for this step.
You may also want to include a set of guiding principles as part of the cybersecurity strategy vision to provide guardrails during the planning process. Examples of such principles include:
Information owners are accountable for protecting information and information resources. In cases of shared information and resources, the CIO is the proxy owner.
The enterprise risk appetite informs all security decisions, and all security controls will be commensurate with the related risk.
The cybersecurity program will document policies, standards, guidelines and procedures that communicate security requirements and guide the selection and implementation of security control measures.
Assess the current state of cybersecurity and prioritize which gaps to fill
Once you have defined the vision for the cybersecurity strategy, you will want to identify the gaps between vision and reality.
Use different assessment types to capture the current state. Map the results against the vision statement as part of a gap analysis. Each gap represents a potential action or initiative you may pursue to achieve the vision.
Few organizations have the resources to narrow all the identified gaps in one planning period. Set priorities depending on the level of risk, the required resources and the time-to-value for each one. Include longer and shorter time-to-value projects within the planning period. These priorities, mapped based on the timelines required to execute on them, will populate a cybersecurity strategy roadmap.
Get buy-in from executive leaders on the vision and priorities
With the vision and priorities established, cybersecurity leaders must now communicate the strategy to get buy-in from executive stakeholders.
That communication will typically include a written report and an executive presentation, which describe the current and desired states and how the priorities will help bridge the gaps between them. Focus the presentation on how the projects will contribute to the business value. Explicitly highlight how the cybersecurity strategy aligns with the business strategy.
Even after you gain approval for the strategy, it’s key to establish a quarterly cadence of reporting and communication on progress and challenges. Be clear about:
Expected benefits that were fully or partially realized and those that were not realized
Unexpected benefits and disadvantages that materialized
Projects that are inconclusive
Triggers to security responses or challenges that might require a change to the strategy or in cybersecurity policies
Institute quarterly reviews and scenario-planning workshops to identify what — if any — drivers have changed to trigger adjustments to the current strategy. This review process should also identify any key leading indicators of large-impact external trends or events that will necessitate major security strategy and roadmap changes.
Attend a Conference
Experience IT Security and Risk Management conferences
With exclusive insights from Gartner experts on the latest trends, sessions curated for your role and unmatched peer networking, Gartner conferences help you accelerate your priorities.
Gartner Security & Risk Management Summit
National Harbor, MD

FAQs on cybersecurity strategy
What is a cybersecurity strategy?
A cybersecurity strategy is a comprehensive plan designed to protect an organization's information systems, data and networks from cyberthreats. It aligns with the overall business goals and ensures that the organization can effectively manage and mitigate risks associated with cyberattacks.
How do I develop a cybersecurity strategy?
Cybersecurity strategy planning must maintain clear links between business drivers, objectives, gaps, and specific projects and actions. The strategic planning process must:
Capture the business context, which comprises business, technology and environmental drivers
Define the strategic vision and guiding principles
Assess the current risk and security state
Perform a gap analysis
Prioritize the proposed actions
Obtain executive approval and budget
What are the implications of a cybersecurity strategy on threat intelligence?
A robust cybersecurity strategy significantly impacts threat intelligence by enhancing an organization's ability to detect, analyze and respond to cyberthreats effectively.
Drive stronger performance on your mission-critical priorities.