- Gartner client? Log in for personalized search results.
FAQs Evolving Insights on AI Risk and Governance for CISOs
December 2025
Table of Contents
- How can CISOs most effectively help to govern AI?
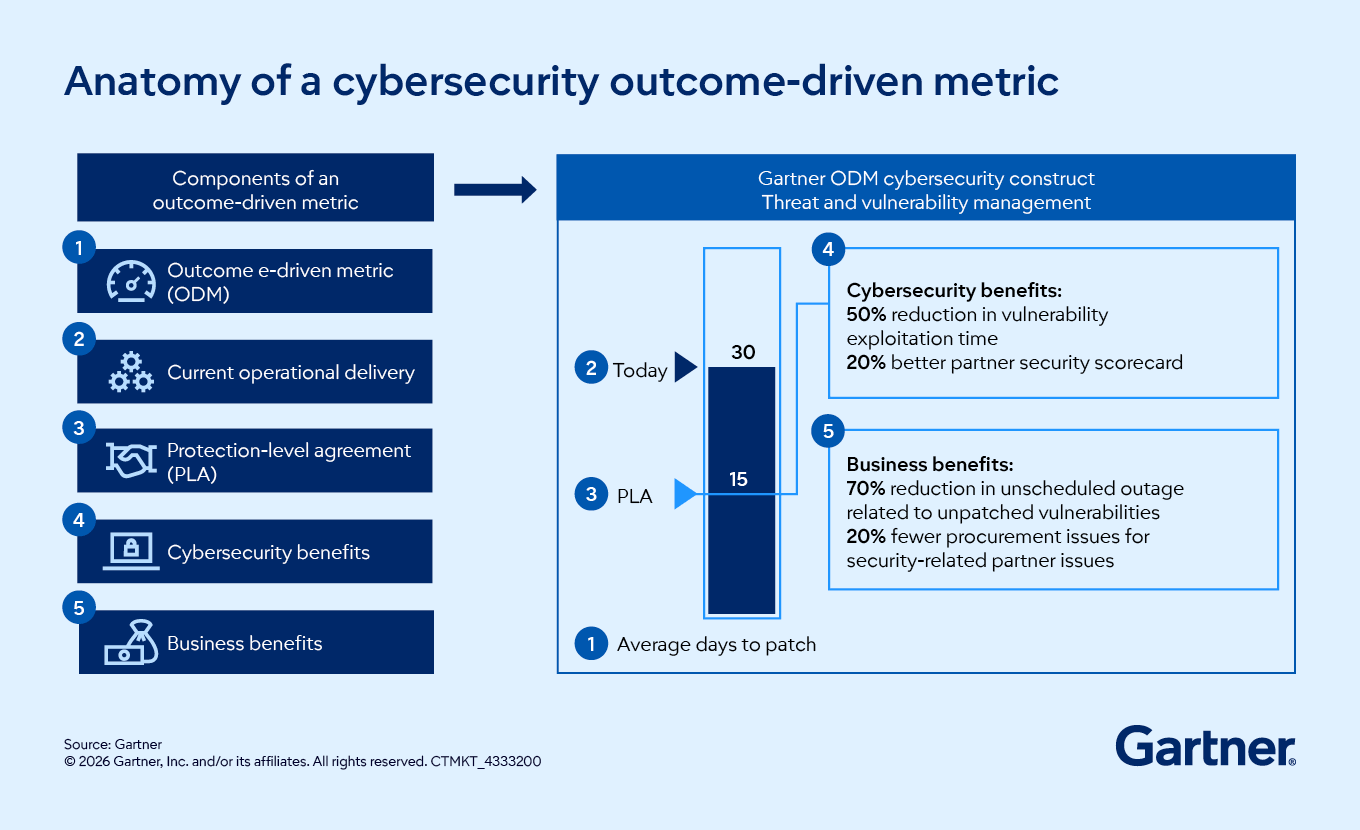
- How can CISOs tailor cybersecurity metrics to most effectively communicate to the board?
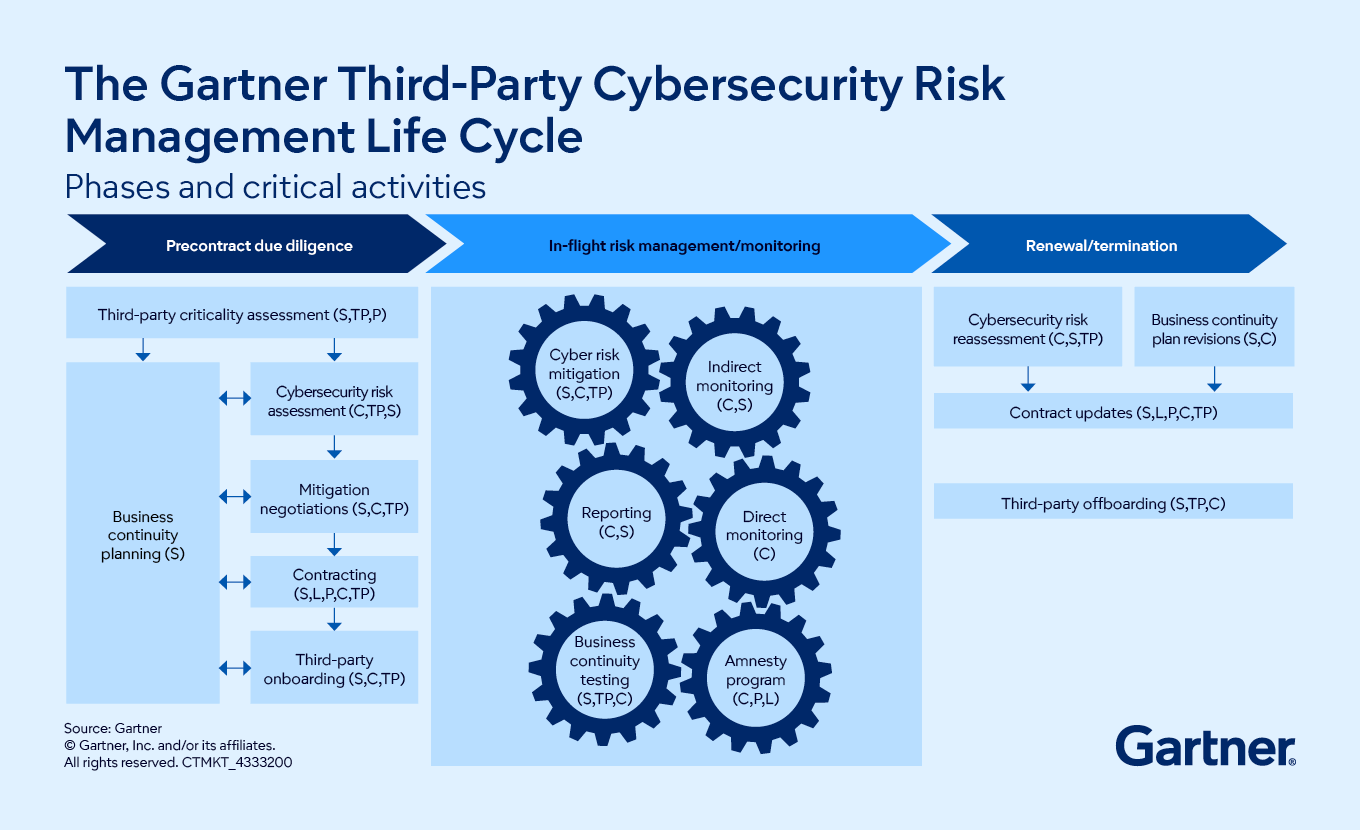
- What are business owners’ responsibilities in managing third-party cyber risk?
- What are cybersecurity leaders’ top AI-related cybersecurity threats?
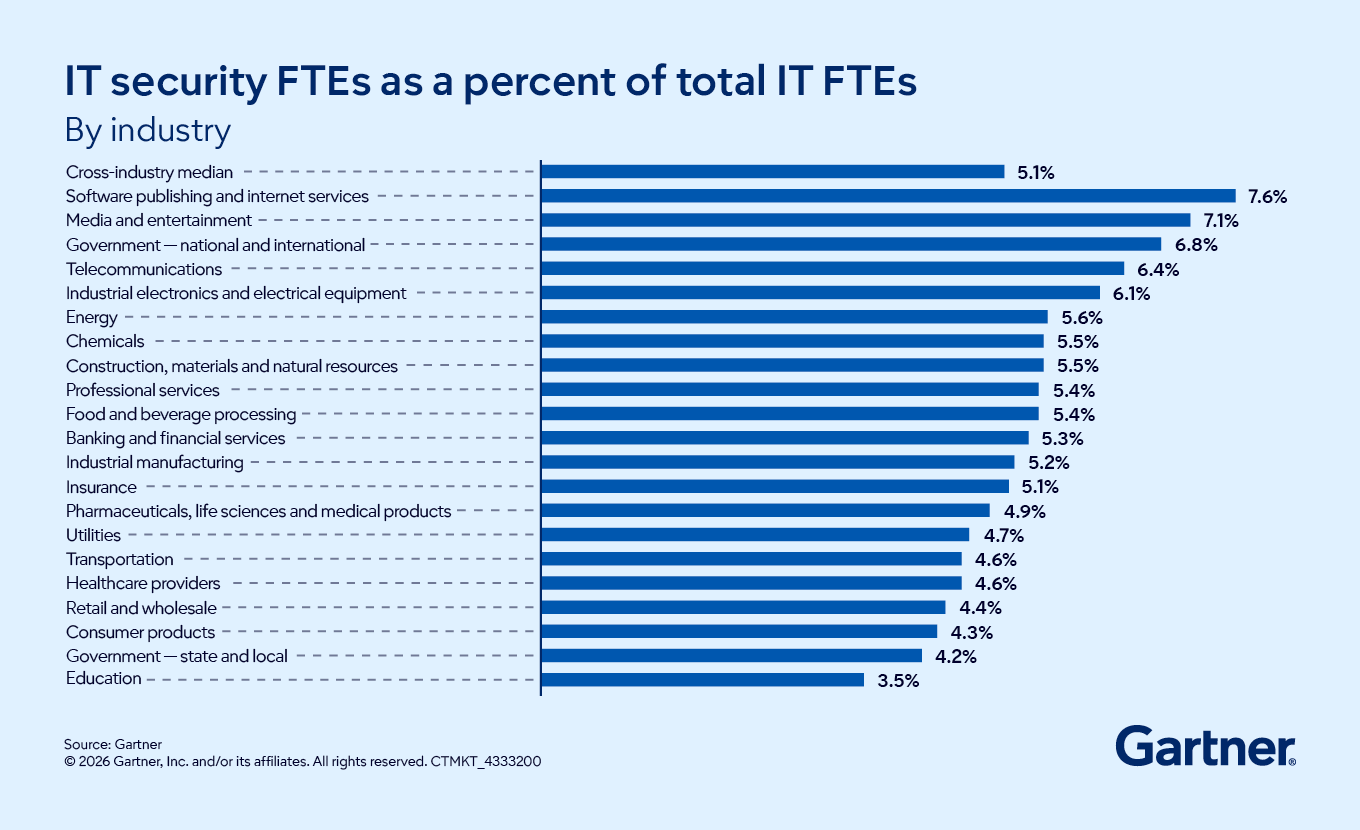
- What is the ideal size of a cybersecurity team?
- What are the most important features of a zero-trust network solution?
Attend a Conference
Accelerate growth with Gartner conferences
Gain exclusive insights on the latest trends, receive one-on-one guidance from a Gartner expert, network with a community of your peers and leave ready to tackle your mission-critical priorities.

Drive stronger performance on your mission-critical priorities.